- IT Solutions
Letʼs take care of your IT so that you can focus on what matters most—your business growth
Enhance your business efficiency with our scalable cloud solutions designed for seamless integration and growth.
Protect your digital assets with our advanced cybersecurity services, ensuring safety in an unpredictable world.
Transform your business with our expert IT consulting, delivering innovative solutions tailored to your needs.
Latest Insights
Case Study
Offshore Managed IT Services to a Leading RPO
The client offshored their Managed IT needs to IMS Nucleii. We brought the response time down from 12 minutes to less than a minute and resolution time from 5h 31m to 2h 3m.
- Sector
Streamlining IT in healthcare, so you can save more lives.
Securing your IT needs, letting you manage financial futures safely.
Enhancing real estate solutions with superior IT service management.
Enhancing real estate solutions with superior IT service management.
Dependable IT support for efficient public service and governance.
Optimizing recruitment and HR processes through expert IT support.
Empowering SMB growth with scalable, reliable IT solutions.
- Work Process
- Resources
Next-Gen Quantum Technologies Powered by Cloud Computing
Quantum computing is an emerging technology that promises revolutionary capabilities by leveraging the bizarre...
Read MoreExplore our collection of free ebooks & Whitepapers around everything IT.Explore a selection of Case Studies highlighting how our innovative solutions.IMS TechExpress is a bimonthly global Tech Newsletter.Zero installation Web Apps for niche purposes. - About
Understanding Malware-as-a-Service


Money is the root of all evil, including cybercrime. Thus, it was inevitable that malware creators would one day begin not only to distribute malicious programs themselves, but also to sell them to less technically proficient attackers, thereby lowering the threshold for entering the cybercriminal community. The Malware-as-a-Service (MaaS) business model emerged as a result of this, allowing malware developers to share the spoils of affiliate attacks and lowering the bar even further. We have analysed how MaaS is organized, which malware is most often distributed through this model, and how the MaaS market depends on external events.
Results of the research
As per studies from various sources, including the dark web, identified 97 families spread by the MaaS model from 2015 and broke these down into five categories by purpose: ransomware, infostealers, loaders, backdoors, and botnets.
As expected, most of the malware families spread by MaaS were ransomware (58%), infostealers comprised (24%), and the remaining (18%) were split between botnets, loaders, and backdoors.
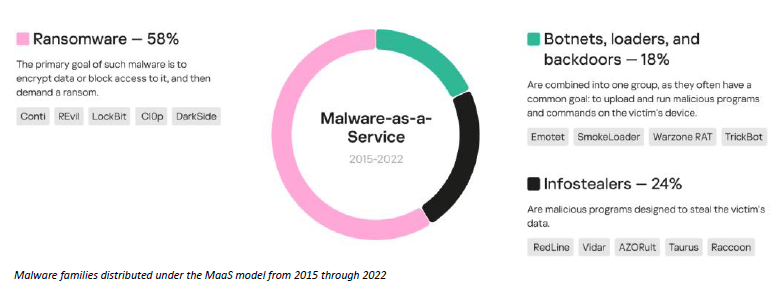
Despite the fact that most of the malware families detected were ransomware, the most frequently mentioned families in dark web communities were infostealers. Ransomware ranks second in terms of activity on the dark web, showing an increase since 2021. At the same time, the total number of mentions of botnets, backdoors, and loaders is gradually decreasing.
MaaS terminology and operating pattern
Malefactors providing MaaS are commonly referred to as operators. The customer using the service is called an affiliate, and the service itself is called an affiliate program. We have studied many MaaS advertisements, identifying eight components inherent in this model of malware distribution. A MaaS operator is typically a team consisting of several people with distinct roles.
For each of the five categories of malware, we have reviewed in detail the different stages of participation in an affiliate program, from joining in to achieving the attackers’ final goal. We have found out what is included in the service provided by the operators, how the attackers interact with one another, and what third-party help they use. Each link in this chain is well thought out, and each participant has a role to play.
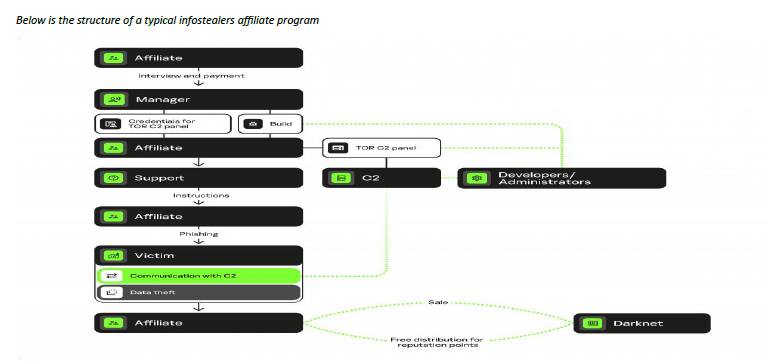
Cybercriminals often use YouTube to spread infostealers. They hack into users’ accounts and upload videos with crack ads and instructions on how to hack various programs. In the case of MaaS infostealers, distribution relies on novice attackers, traffers, hired by affiliates. In some cases, it is possible to de-anonymize a traffer by having only a sample of the malware they distribute.

Join Us To Get Update
Corporate Office
1/2, Indraprasth Business Park,
Near DAV School, Prahladnagar Extension, Makarba, Ahmedabad- 380051, Gujarat, India.














