Managed Detection and Response (MDR) has emerged as а pivotal strategy in bolstering organizational cybersecurity postures. MDR involves outsourcing detection and response capabilities to security experts through а managed service model. It marries automation with human intelligence to proactively identify, analyze and address threats across an enterprise’s digital infrastructure. As attacks evolve in complexity and scale due to the rising exploitation of artificial intelligence, machine learning and work-from-home trends accelerated by the pandemic, adapting defensive measures through MDR has become imperative.
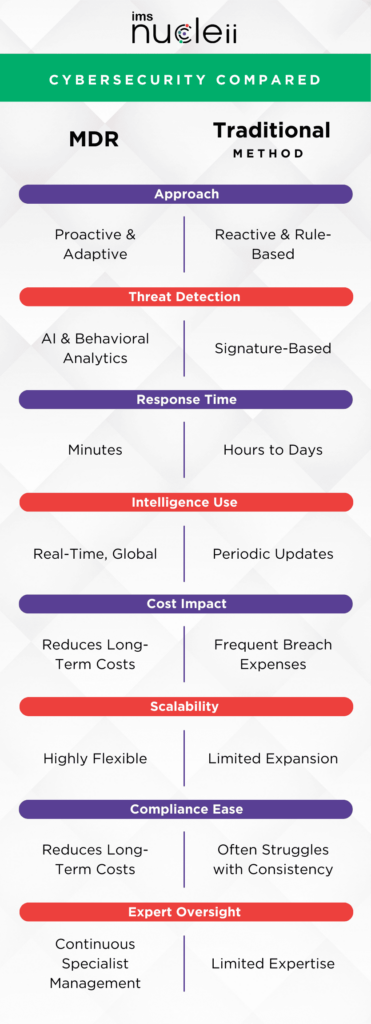
Traditional security approaches mostly rely on preventative controls like firewalls, antivirus, and intrusion prevention systems (IPS). While such controls form the foundation, modern threats circumvent them with advanced evasion techniques. MDR transcends the limitations of conventional point solutions through comprehensive monitoring, early detection of known and unknown threats, and rapid containment of active incidents. This article analyzes how MDR has emerged as the preferred strategy to reshape cyber defenses aligned with evolving adversarial TTPs (tactics, techniques and procedures).
The Imperative for MDR
Since the onset of digital transformation, cyber risks have multiplied manifold with multiple entry points and vast attack surfaces. Simultaneously, threat actors have scaled operations leveraging underground markets for malware, open-source intrusion frameworks and outsourced labor. Ransomware, for instance, has burgeoned into а multi-billion-dollar criminal economy through RaaS (Ransomware-as-a-Service) affiliates readily weaponizing advanced evasion techniques and exploit kits.
Traditional security approaches relying on preventative controls alone have grown insufficient against such sophisticated, multi-staged campaigns. While managed security service providers (MSSPs) offer outsourced monitoring and management, their reaction times remain high due to reliance on rules-based detection. MSSPs also lack the predictive capabilities and human oversight required to proactively identify unknown threats indicating advanced persistent attacks (APT).
The dynamic, hybrid workforce model further exacerbates risks with personal and IoT devices directly interacting with business-critical systems. Work from home has made traditional perimeter-based defenses defunct by eradicating network boundaries. These shifts necessitate а proactive, enterprise-wide perspective for early detection of internal compromises and supply chain infiltrations before damage. MDR addresses such limitations through its predictive, holistic methodology.
Core Components of MDR Services
MDR leverages cutting-edge technologies, exploits and human security expertise to continuously hunt for known and unknown threats across clients’ IT environments. At the core of MDR operations are:
- 24/7 Monitoring and Response: Experienced SOC analysts aided by security orchestration tools monitor endpoints, networks and applications around the clock. They analyze incidents, prioritize critical risks and remediate threats according to documented runbooks.
- Proactive Threat Hunting: Threat-hunting security experts actively search for obfuscated indicators of compromise (IoCs) and scan environments using YARA rules and proprietary methods to uncover hidden infections indicating advanced adversaries.
- Incident Investigation and Remediation: Once detected, analysts forensically review all associated events and perform root cause analysis to conclusively characterize threats. They then develop coordinated containment and eradication plans for swiftly resolving security breaches.
- Integration of Advanced Technologies: MDR stacks leverage machine learning algorithms, behavioral analytics, and big data frameworks to identify anomalies, correlate dispersed IoCs, and precisely attribute activity to malicious campaigns or individual actors. This powers predictive threat detection capabilities.
Operational Advantages of MDR
MDR substantially enhances organizations’ level of visibility and security posture through its predictive, enterprise-wide methodology. Some key operational benefits include:
- Enhanced Detection: Comprehensive monitoring across endpoints, networks, applications and infrastructure with continuous log analysis yields far richer insights than selective point solutions. AI/ML-powered correlation hunts for even stealthy threats.
- Rapid Response: Analyst-supported monitoring and workflows ensure incidents are addressed within minutes through pre-mandated runbooks, versus hours or days for self-managed detection and response. This minimizes breach impact and scope.
- Proactive Posture: Continuous threat hunting uncovers even subtle, long-running campaigns that evade rules-based tools. It predicts emerging risks and adversaries’ next moves by attributing activity to known APT groups based on behavioral patterns and exploited vulnerabilities.
- Lesser Dwell Time: With prompt detection and containment, MDR lowers the time period during which adversaries maintain footholds unnoticed to steal data or laterally move within the network. This closes а major attack vector.
- Reduced Overheads: MDR teams handle Security Operations Center (SOC) tasks, allowing internal staff to prioritize strategic initiatives. It also negates large hiring, training and infrastructure costs for developing in-house SOC capabilities.
Strategic Benefits of Adopting MDR
Adopting а managed MDR service conveys multifaceted strategic benefits that strengthen overall security postures and maximize risk management.
- Cost-Effectiveness: By consolidating detection/response resources, MDR lowers overall security expenditures considerably compared to purchasing distinct point solutions, bolstering staff and tools individually.
- Scalability: Services adjust quantity and type of coverage according to evolving needs, from monitoring а basic server configuration to multi-cloud, IoT-enabled environments. Payments scale in tandem through flexible contracts.
- Compliance: MDR speeds audit processes by centralizing logs/artifacts and demonstrating protection standards adherence through policies, analytics reports and incident responses adhering to frameworks like NIST, ISO etc.
- Mitigated Disruptions: Quick detection/containment via MDR supports continuity of operations and prevents financial losses due to ransomware payment demands or customer data breaches damaging brand reputation.
- Improved Visibility: MDR providers maximize sensors, analytics and expertise over clients’ dispersed IT assets for detecting even obscure threatsIndicators otherwise escaping isolated monitoring tools with blind spots.
- Mobility: MDR’s vendor-managed, subscription model mitigates overdependence on in-house staff availability. Security postures remain reliable regardless of workforce schedules, remote work or attrition.
MDR Vs. Other Security Solutions
While MDR rises as the preferred strategic shift, it succeeds with legacy and complementary solutions versus replacing them. Below are some contrasts:
- MDR vs. MSSPs: Unlike MSSPs focusing narrowly on operations, MDR providers actively hunt for known and unknown threats 24/7. MDR’s predictive, expert-augmented stance surpasses reactive rule-based monitoring.
- MDR vs. EDR: Endpoint Detection and Response software is limited to endpoints versus MDR’s integrated protection of all IT assets through network segmentation, application controls etc. MDR also leverages broader datasets and threat intelligence.
- MDR vs. SIEM: While Security Information and Event Management platforms collect telemetry, MDR analysts leverage SIEM forensically during investigations versus relying on SIEM alerts alone which fail to identify silent adversaries.
- MDR Augments Security Stack: By seamlessly extending detection surfaces and response functions firmwide, MDR strengthens existing measures like firewalls, antivirus, XDR and identity management rather than displacing them. It knits them into а cohesive cyber defense fabric.
Choosing the Right MDR Provider
With MDR emerging the go-to strategy, selecting the right provider undergirds optimizing its security value proposition. Key considerations include:
- Expertise and Track Record: Look for а proven specialty MDR company with deep experience within target industries and certifications like CISSP among its security researchers and SOC analysts.
- Customizability: Check compatibility with current security tools and configurable service coverage meeting unique needs depending on risk thresholds, budget and compliance requirements.
- Integration Capabilities: Ask how well the vendor integrates deployed sensors, telemetry centralization and proprietary technologies into clients’ systems for consolidated visibility and optimized response coordination.
- Scalability: Inquire about elastic service tiers, plans and partnerships for scaling protection as needs evolve by expanding IT footprints or as threats intensify regionally.
- Support Quality: Assess response times, available support channels and partnerships or alliances broadening solutions acumen for complex incidents.
- Communication: Transparency into reporting, ticket management and regular reviews showcasing response metrics, new threats and enhancement road maps indicating accountability.
- Cost-Efficiency: Weigh contract flexibility, and automation enabling managed services to eventually match growing in-house staff and infrastructure costs which hamper strategic objectives.
An ideal choice is IMS Nuclei – а leader in proactive defense against both known and unknown threats. IMS Nuclei’s team of experts and industry veterans, specialized in delivering unparalleled detection expertise through customized MDR, backed by а proprietary AI/ML-powered platform. Their integration, scalability, compliance and communications support make them the top MDR partner for optimizing cyber risk postures amid disruptive changes.
Conclusion
As businesses go digital and the threat landscape evolves, robust defense strategies must evolve correspondingly. MDR has emerged as the optimal model aligning prevention, early detection and efficient response capabilities with proliferating, sophisticated cyber adversaries. By outsourcing predictive security to dedicated, expert-augmented MDR services like IMS Nuclei that continuously learn evolving TTPs.












